Documentation This documentation applies only to iceScrum v7.
For old iceScrum R6, read the documentation or migrate.
The General Data Protection Regulation (GDPR) is a European Union (EU) regulation on data protection and privacy for all individuals within the European Union. Read this documentation to learn how iceScrum complies with this regulation.
Cloud / Website
To know how we ensure the privacy of your personal data if you use our Website / Cloud platform, read our privacy policy. To exercise your rights, please contact our team at privacy@kagilum.com, we will be glad to help.
On-Premise
This section applies only to the use of self hosted iceScrum servers (= On-Premise). If you use iceScrum Cloud or if you are registered on our website, refer to the previous section.
As defined in the regulation, “‘personal data’ means any information relating to an identified or identifiable natural person”. Our tool is targeted at organization rather than individuals, so personal data is only a very small part as the data managed in iceScrum, and there is no automated processing for user profiling purposes.
If you host an iceScrum server and have users in the EU, then you must comply to this regulation regarding the personal data stored on your server.
We wrote this guide to help you comply with the GDPR, but a tool cannot do everything for you and we strongly recommend that you take your own measures to ensure that you fully comply.
Personal data collection, use and processing
As suggested above, iceScrum stores very little data on its users. For non-registered and disconnected users, there is no personal data storage or processing at all. For registered users, the following personal information is stored:
- Username – required
- Email address – required
- Password – required if internal, not used otherwise (LDAP, AD, SAML, SSO) – strongly encrypted
- First name – required
- Last name – required
- Language – required
- Avatar – optional
- Activity – optional
iceScrum also records very basic meta-data such as the last project opened and a few dates: creation, last update, last connection, last time notifications were read. Our tool also provides integrations with other tools, and in such case require credentials to connect to these tools, which may personally identify someone.
Cookies and browser local storage are not used to store personal data / profile users, so they don’t require consent. Email addresses are used only if configured by the server administrator, and only to send notifications about data updates in iceScrum for items users have shown interest in.
And that’s about it, iceScrum does not process this personal data automatically for user profiling, nor does it send it to our servers apart from very limited circumstances with logs defined in the paragraph below. There is nothing shady such as the big data AI processing for marketing/advertisement you can find in too many applications nowadays…
When an unexpected error occurs when a user enters data, depending on the level of logs chosen by the administrator, this data (password excluded) may be written in the logs (iceScrum / Tomcat logs) to help troubleshoot the issue. Such data may contain personal data. If your server is connected to an email server, then the error logs are sent by email to your server administrators. It is also sent to the email address configured by icescrum.alerts.errors.to in your config.groovy, which defaults to our development team: dev@icescrum.org but can be changed by the administrator. If we receive such data, we only use it on a case by case basis to understand and fix bugs to improve your experience with iceScrum!
We recommend exposing your server only to the extent that it is necessary (e.g. on a private network) and to expose your server only through SSL/HTTPS through a proper certificate. Nothing is 100% secure, but we do our best to make iceScrum as secure as possible. It is your responsibility to ensure that your infrastructure also aligns with the best security standards (e.g. SSH access to server, strong passwords, allow connections to the database only from the iceScrum server…).
User rights
In addition to the limitation of processing, individuals have several rights on their data under the GDPR: access, rectification, erasure, portability…
Most data entered by a user can be seen and updated by this user. For the rest and user deletion, a link at the bottom of the user profile allows the user to contact the server administrator by email.
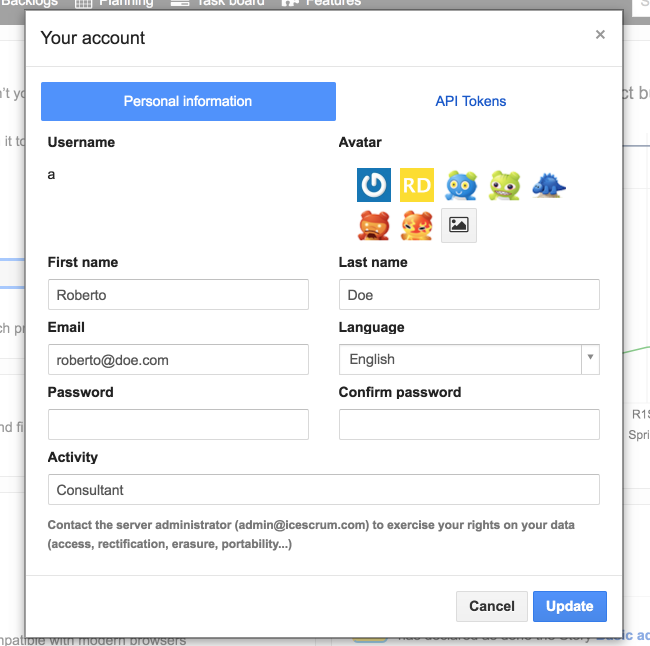
The administrator account has all permissions on all iceScrum data, including users and projects. User administration is done either through the dedicated UI if you have a paying license, or only via the REST API if you don’t.
Administrator permissions include the ability to retrieve and update user data, but also to remove the user and most personal data alongside with it. You can remove the projects and teams owned by a user. However, they may also contribute to other projects and it is not desirable to delete this data. For such data, iceScrum rather relies on anonymization: data is transferred to a dedicated “ghost” account of your choice so it can no longer be attributed to the original data subject.
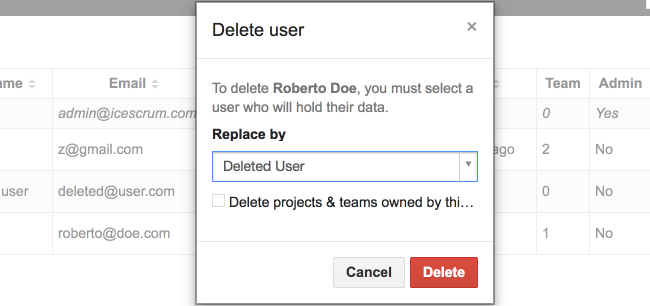
Please note that nothing prevents users to enter personal data in other textual fields such as comments, stories, etc. or in attachments. You should handle that on a case by case basis.
If the tools provided by iceScrum are not enough, you can look for user data in three places:
- Directly in the iceScrum database for textual data,
- iceScrum / tomcat logs,
- iceScrum base directory and its subdirectories.
Of course, depending on your infrastructure, user personal data managed in iceScrum may also be stored in backups, reverse proxy logs, etc.
If the above is not enough for you to fully comply and that you think we can help, contact us.